Contents
Docs
General
- Introduction
- What is Android Enterprise?
- Android versions matrix
- Considerations when migrating from device administrator to Android Enterprise
- Android Enterprise feature requests
- What is Android Enterprise Recommended?
- Android Enterprise FAQ
- Android Enterprise device testing
- What is Private Space in Android 15, and how can organisations manage it?
- Why don't all Android devices come with GMS?
- What is Android One?
- Android Enterprise vs Device Admin: Why DA is no longer suitable
- Considerations for choosing Android in the Enterprise
- Feature spotlight: Android Smartlock
- Android glossary
- Android version evolution graphics
- Infobyte: Device Admin deprecation
- How to submit a device for Android Enterprise Recommended validation
- How to view software version information
- How to capture a bug report and device logs
- Gartner comparison of security controls for mobile devices 2019
Provisioning
- How to become a zero-touch enrolment reseller
- What is Android zero-touch enrolment?
- Android Enterprise zero-touch console administration guide
- Android Enterprise DPC identifier collection
- Android Enterprise provisioning guides
- Android Enterprise zero-touch DPC extras collection
- Infobyte: Android Enterprise deployment scenarios
- Infobyte: Android Enterprise fully managed provisioning methods
- Manual Android Enterprise work-managed QR code generation for MobileIron
Work profile
Fully managed
App management
- Set up Hypergate's Kerberos Authentication on MobileIron Core for Android Enterprise
- Managed Google Play, allowlist or blocklist?
- Considerations when deploying MTD with Android Enterprise
- Why you shouldn't install apps from unknown sources
- Create and manage private apps for Android Enterprise
- What is OEMConfig?
- Create and manage web apps for Android Enterprise
- How to locate a private Android app assigned to an organisation ID
- How to host enterprise apps outside of Google Play
- The Google Play iFrame app approval flow is deprecated
- Android 13 adds notifications access as a runtime permission
- Android 14 blocks apps targeting old Android versions
- Android 13 & up restricts permissions when apps are sideloaded
- Android system apps database
- How to resolve common Android app install failures, by error message
FAQ
- Is Android Enterprise supported on uncertified (non-GMS) devices?
- Can apps be sideloaded into the Private Space?
- Is Private Space supported on fully managed devices?
- Why don't Private Space apps go through VPN?
- Is it possible to manage personal applications on a work profile device?
- Does Samsung support Android Enterprise?
- How can apps be managed in the Private Space?
- Are Private Space apps visible to enterprise admins?
- Are Private Space applications truly hidden?
- Why has USB data access been disabled suddenly?
- What versions of Android support Android Enterprise?
- Is it possible to manage eSIM?
- How to check if an Android device is GMS/Play Protect certified?
- To use Android Enterprise do I need to buy Google Workspace (G Suite) and register my domain?
- What devices should I buy for my organisation?
- If Android Enterprise is supported from Lollipop, why is Marshmallow often mentioned instead?
- What’s the difference between Device Admin and Android Enterprise?
- What is the Android Enterprise bind?
- Can I change the account I used to bind Android Enterprise?
- Is it possible to bind Android Enterprise with multiple EMMs using one account?
- How do I remove the Android Enterprise bind from my current EMM?
- What is Android Enterprise Recommended?
- My AER device doesn’t work properly with Android Enterprise, what should I do?
- Is Android One better than AER? (Or the other way around?)
- How do I configure Google Workspace domains for provisioning?
- What’s the best provisioning method?
- What’s the difference between allow adding accounts vs allow configure credentials?
- Is it possible to utilise multiple VPN connections within a profile?
- Is it possible to utilise a single VPN connection across the entire device?
- Does Android support Kerberos natively?
- What’s the difference between device based accounts and user based accounts?
- How do I manage the new notifications runtime permission in Android 13?
- Can organisations see applications outside of the work profile?
- Can organisations deploy applications to the parent profile in a work profile deployment?
- Is it possible to migrate from DA to AE work profile without a re-enrol?
- What is a work challenge?
- Enrolment failed but the work profile was created. How do I remove it?
- Why can’t I install or uninstall apps on my managed device?
- How can I provision a fully managed device?
- Is it possible to “retire” (or enterprise wipe) a fully managed device?
- Devices factory reset as soon as they’re enrolled, why?
- Is Factory Reset Protection enabled on fully managed devices?
- Is it possible to migrate fully managed devices between EMM solutions?
- How has COPE changed in Android 11?
- Does Intune support COPE?
- Can organisations see applications outside of the work profile on a COPE device?
- Can organisations deploy applications to the parent profile in a COPE deployment?
- Is it possible to migrate from fully managed to work profiles on fully managed devices?
- How should system applications be handled on a COPE device?
- What OEMs currently support zero-touch?
- Where are zero-touch resellers located?
- Does zero-touch cost anything?
- Is an EMM still required with zero-touch?
- What happens if a fully set up device is added to the zero-touch console?
- What happens if a user starts setting up a device before the zero-touch config is applied?
- What happens if a zero-touch config is removed from an enrolled device?
- What happens if a new config for a different EMM or server is applied to an enrolled device?
- Can I add/remove users on a fully managed device?
- How can I access a Wi-Fi captive portal when devices are in Kiosk?
- My AMAPI project returns a usage limit error, why?
- What happens if a zero-touch assigned device is reset?
- What happens if a device is unregistered from the zero-touch console?
- Can a device be OTA managed from the zero-touch console?
- Does enrolling via zero-touch slow down or cause any delay to the setup process while it’s retrieving the zero-touch config?
- What deployment scenario will a zero-touch device enrol under?
- Why does zero-touch require so much touching?
- Can anyone add a device to the zero-touch console?
- Is it possible for an organisation to add previously-purchased devices to zero-touch?
- Can a MADA device be converted to EDLA?
- Can anyone remove a device from the zero-touch console?
- Does Samsung support zero-touch?
- Is it possible to set a zero-touch default configuration?
- Is it possible to bulk update zero-touch devices?
- Is it possible to change zero-touch resellers?
- Are all zero-touch devices Android Enterprise Recommended?
- What are DPC extras?
- What should I put in DPC extras?
- What happens if a device is uploaded to zero-touch with the wrong manufacturer?
- The device registered with zero-touch, but doesn’t launch during setup, why?
- Does Android Go support zero-touch?
- Are employee-owned devices eligible for zero-touch?
- What’s the recommended way of managing private (in-house) applications?
- How do I turn off Google Play app collections?
- Is it possible to deploy app shortcuts to the homescreen of an Android Enterprise device?
- Is it possible to backup & restore device data on a fully managed device?
- The Google Play iFrame is missing a feature in my UEM. How do I enable it?
- How do I configure allowlist/blocklist domains for Google Chrome?
- How to configure Chrome managed bookmarks
- Play Protect blocked my DPC, why?
Set up Hypergate's Kerberos Authentication on MobileIron Core for Android Enterprise
Contents
Kerberos authentication is a common method of providing Single Sign On with on-premise Microsoft Active Directory. This kind of authentication is also referred to as Integrated Windows Authentication (IWA) or SPNEGO.
Android Enterprise lacks native Kerberos support, but with a 3rd party solution, in this case Hypergate, it’s possible to fill the native gap. This guide will describe how you can configure MobileIron Core to enable Android Enterprise to simulate Smart Card logons and leverage Kerberos Authentication to extend Single Sign On for corporate services to Android Enterprise devices.
Hypergate is not a free solution, however is priced competitively and sold through a network of partners. More information can be found here.
Prerequisites
#- An existing Kerberos environment in place and functional
- Android Enterprise bound and fully configured
- MobileIron Core configured to leverage Kerberos (SCEP configs in place), and pushing client certificates to devices.
- MobileIron Tunnel
- Hypergate licensed
For context, the environment utilised for this guide is as follows:
- Our Active Directory Domain Controller has the FQDN ‘DC01.MIACME.NL’
- The Realm (aka Domain for MS folks) is ‘MIACME.NL’.
- MobileIron Core is configured to work with a SCEP server and client certificates are already pushed onto the devices.
- MobileIron Tunnel is used to allow the managed device to connect to the KDC (aka Domain Controller for MS folks).
- Hypergate is the Kerberos client other apps will use to request Kerberos tokens.
- The devices are fully managed. though all AE deployment scenarios are supported
Import Google Chrome
#In MobileIron Core head to Apps > App Catalog > Add+ > Google Play and search for Google Chrome.
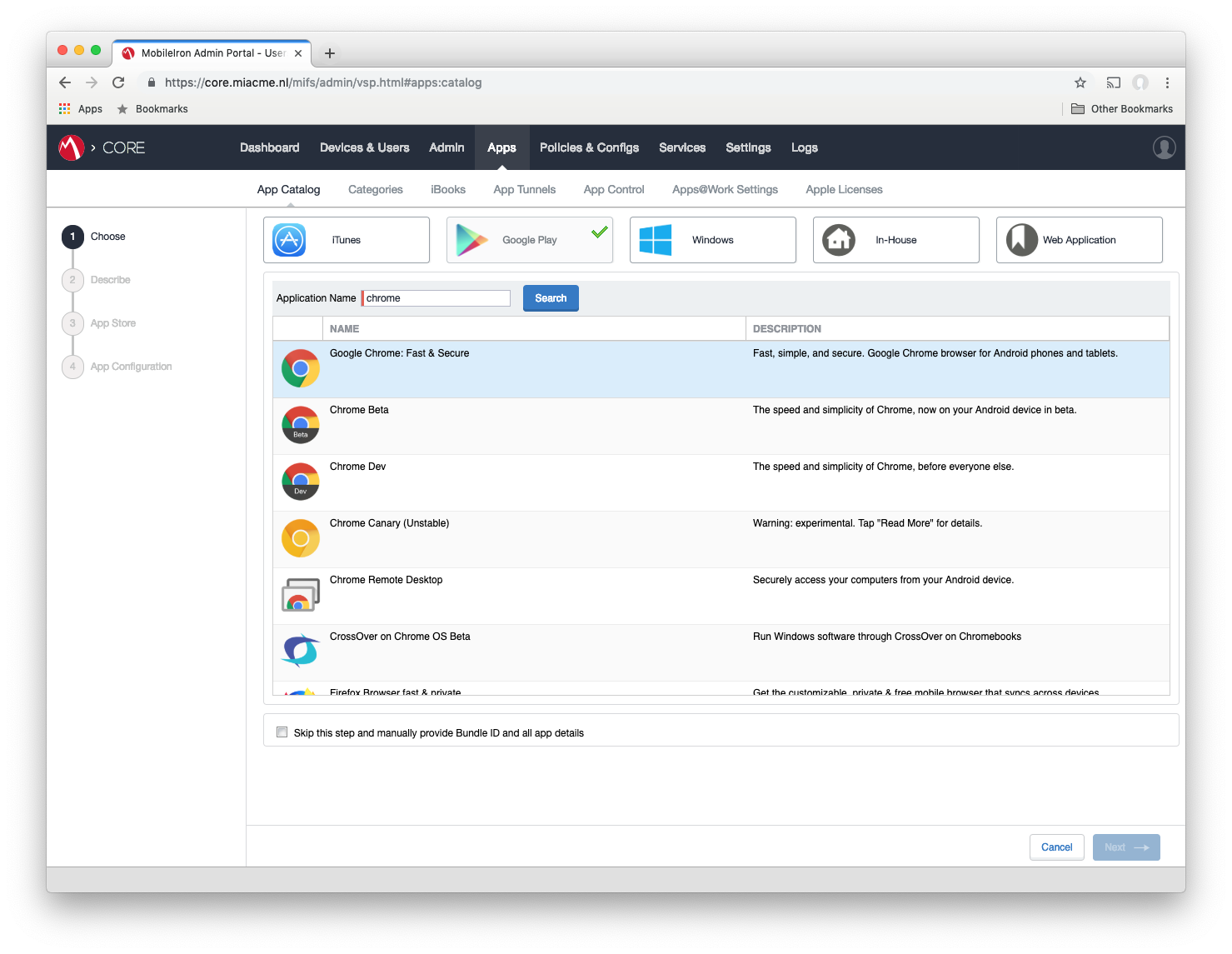
Select the correct App, add it to the Category you want then make sure you tick the box Install this app for Android Enterprise.
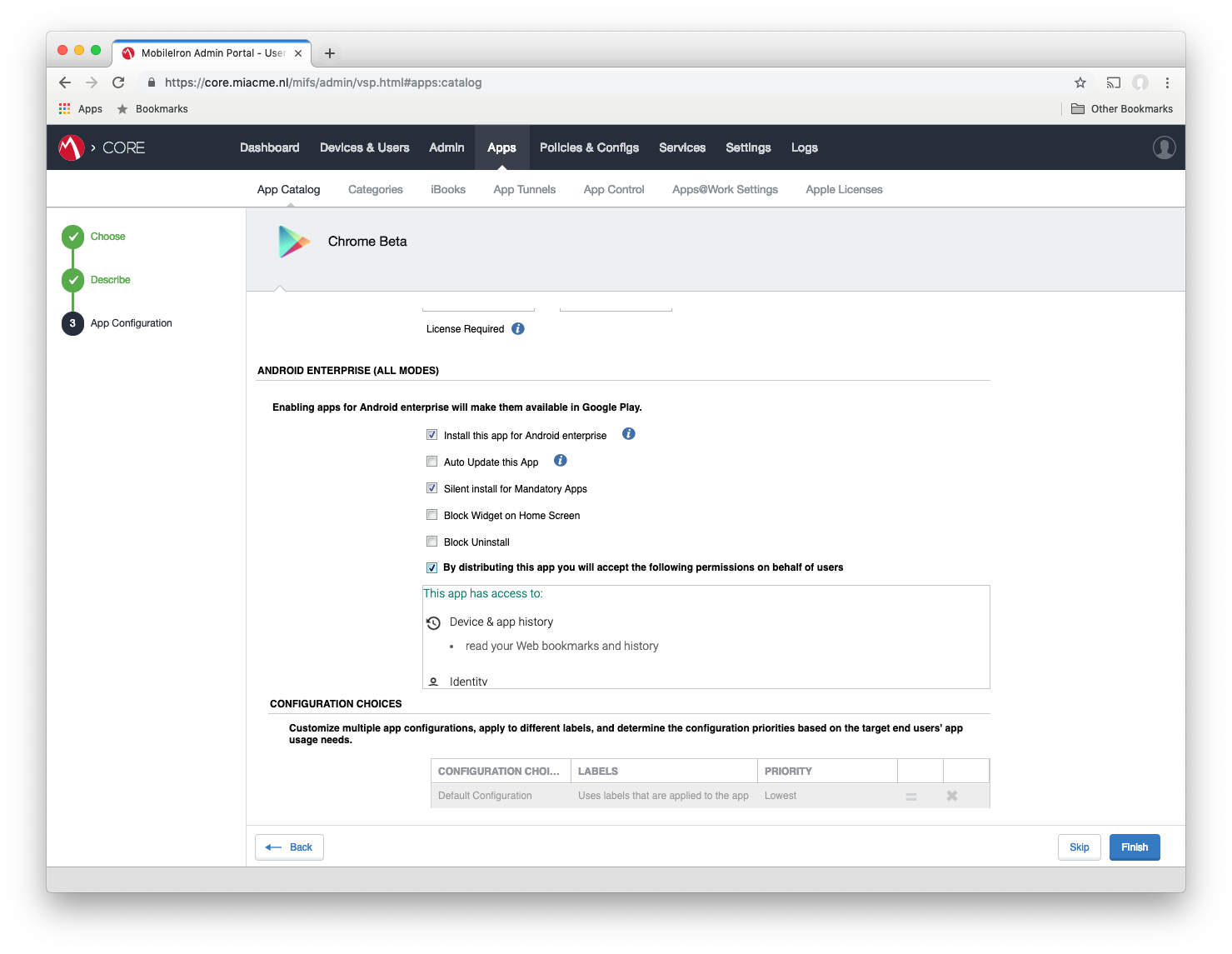
Configure Google Chrome
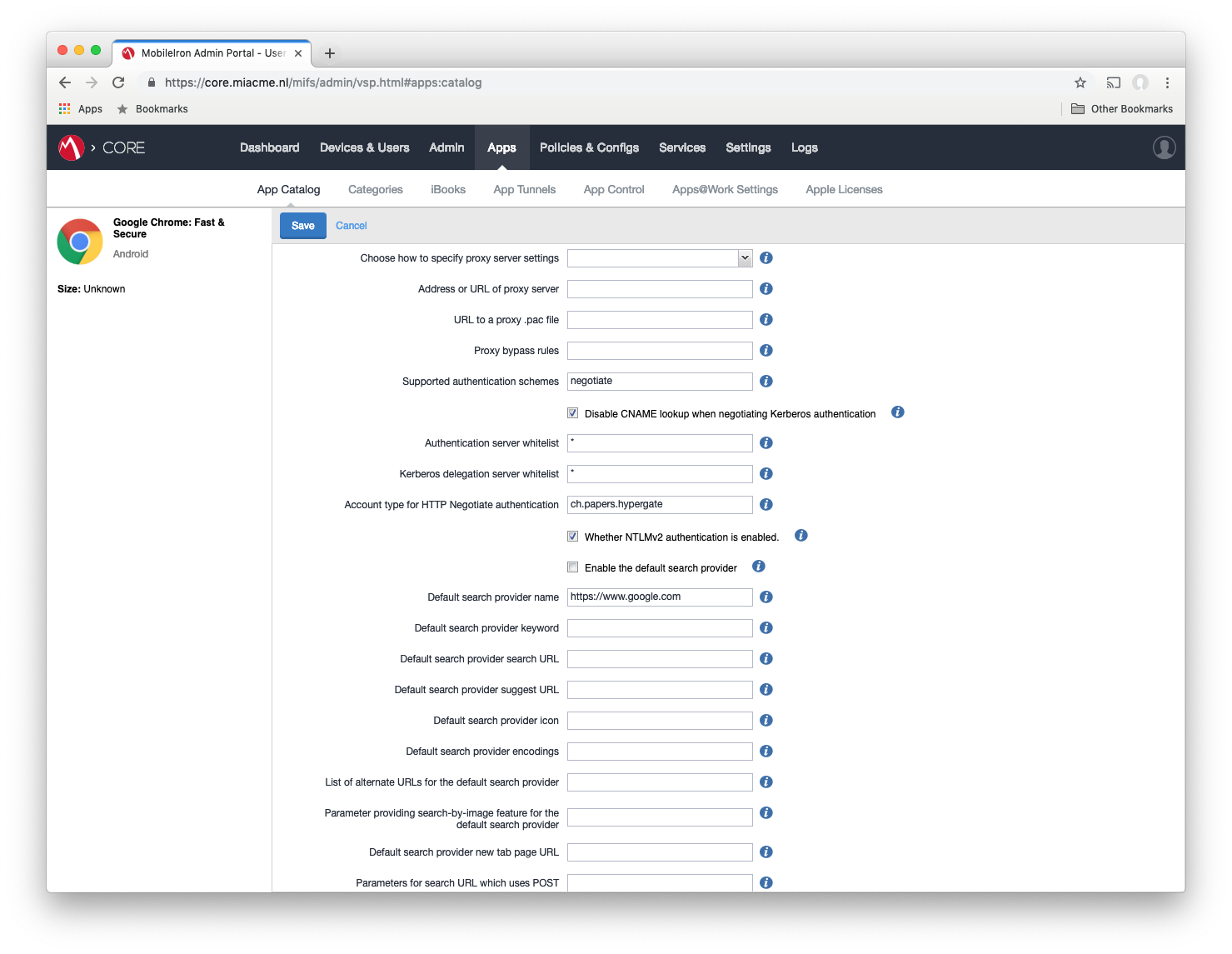
#After ticking the box to enable AE, scroll down to the managed configuration section. The Kerberos relevant configurations are:
- Supported authentication schemes: this needs to be “negotiate” telling Chrome to act accordingly if the Server responds with a Negotiate challenge.
- Authentication server whitelist: this can be a list of all servers permitted to request tokens. Wildcards are also valid. In this guide a wildcard “*” is utilised.
- Kerberos delegation server whitelist: this can be a list of all servers permitted to request tokens. Wildcards are also valid. In this guide a wildcard “*” is utilised.
- Account type for HTTP Negotiate authentication: this tells Chrome where to look for an App that can deal with the negotiate challenge. In this guide “ch.papers.hypergate” is used because that’s how Hypergate advertises itself.
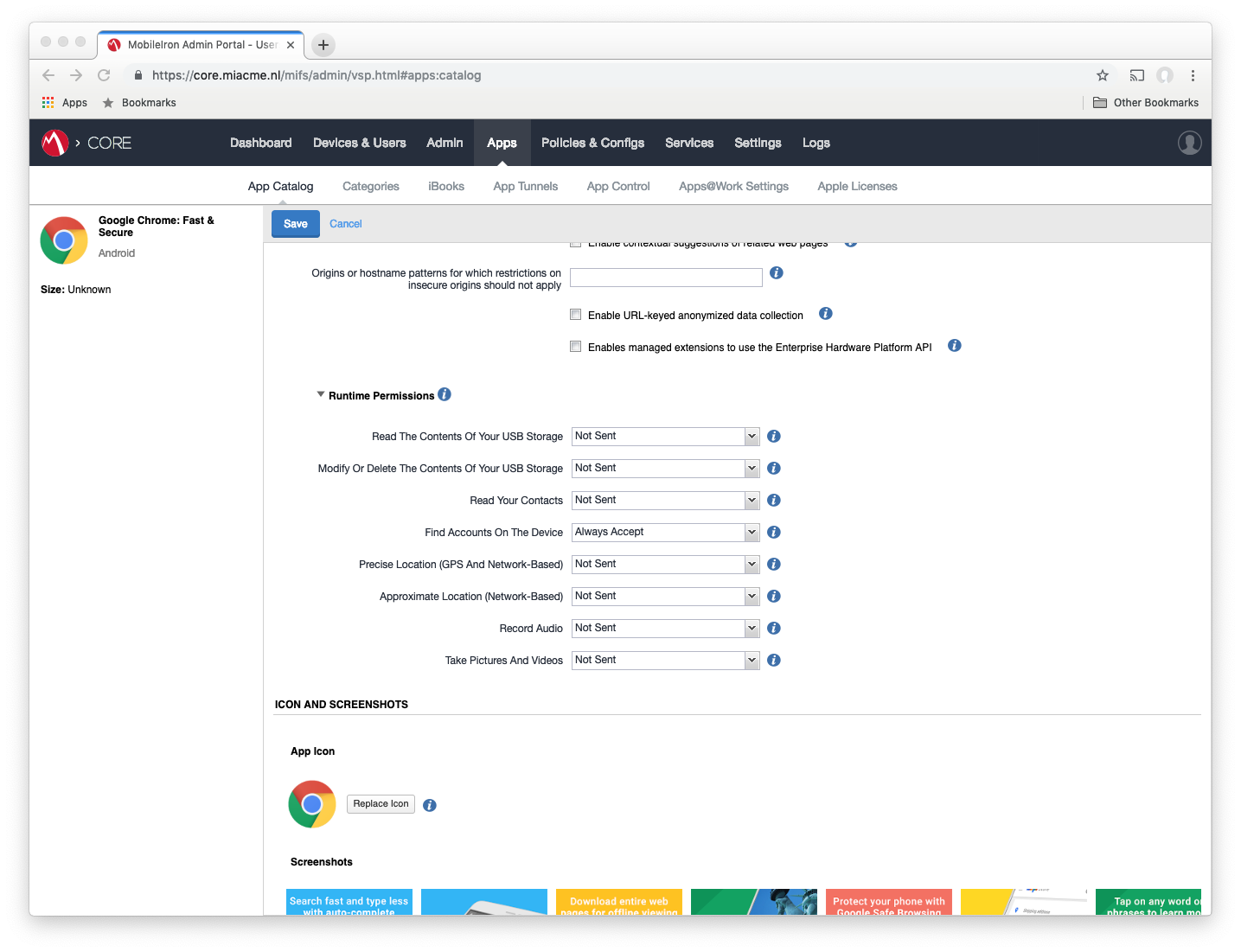
Following this, set the Find Accounts On The Device runtime permission to Always Accept:
Click Finish/Save.
Import Hypergate
#Head to Apps > App Catalog > Add+ > Google Play and tick Skip this step and manually provide Bundle ID and all app details > Next. You will be prompted with a form in which you need to enter the package name provided by the Hypergate team. This is because Hypergate is not visible publicly on Google Play currently.
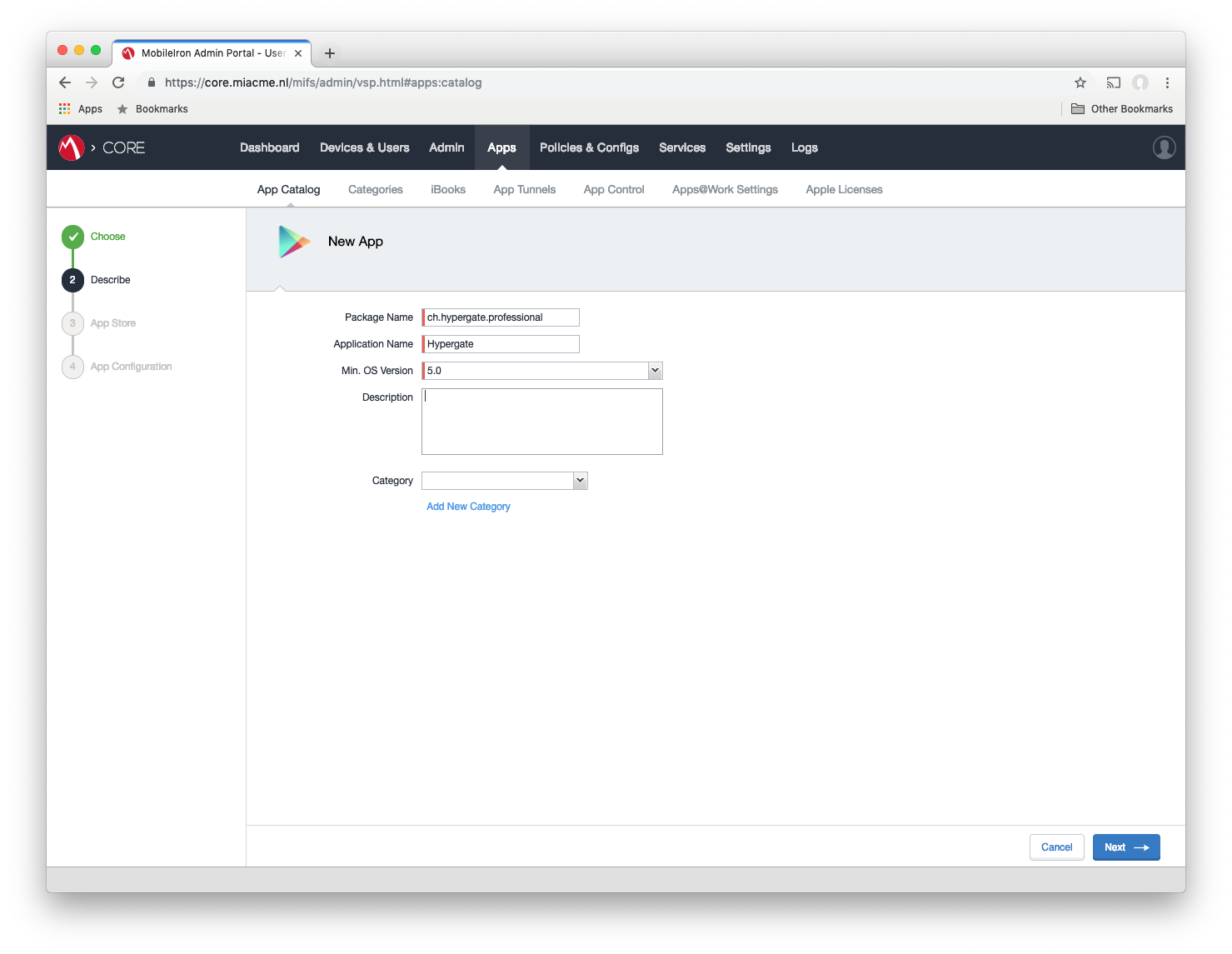
Optional: For easier application list management (distinguish apps easier) you can also set the Hypergate logo in the next form by hitting “Replace Icon” and using this logo:

Click Install this app for Android Enterprise.
Configure Hypergate
#Scroll down to the managed configuration section. The relevant configurations are:
- Username: this should typically be $USERID$, but may need to follow naming conventions used in other SCEP configurations
- Default realm: this is the domain
- Key Distribution Center: this is the Domain Controller’s FQDN
- PKinit KDC Hostname for PreAuth: this is the Domain Controller’s FQDN
- PKinit Certificate Alias: [intentionally blank]
- Certificate Authority: Paste the CA cert, including intermediaries in this field.
- Package name whitelist (comma separated): which apps should be allowed to requests tokens
- Discoverability package names List (comma separated): which apps should discover Hypergate without first prompting the user with a selection screen.
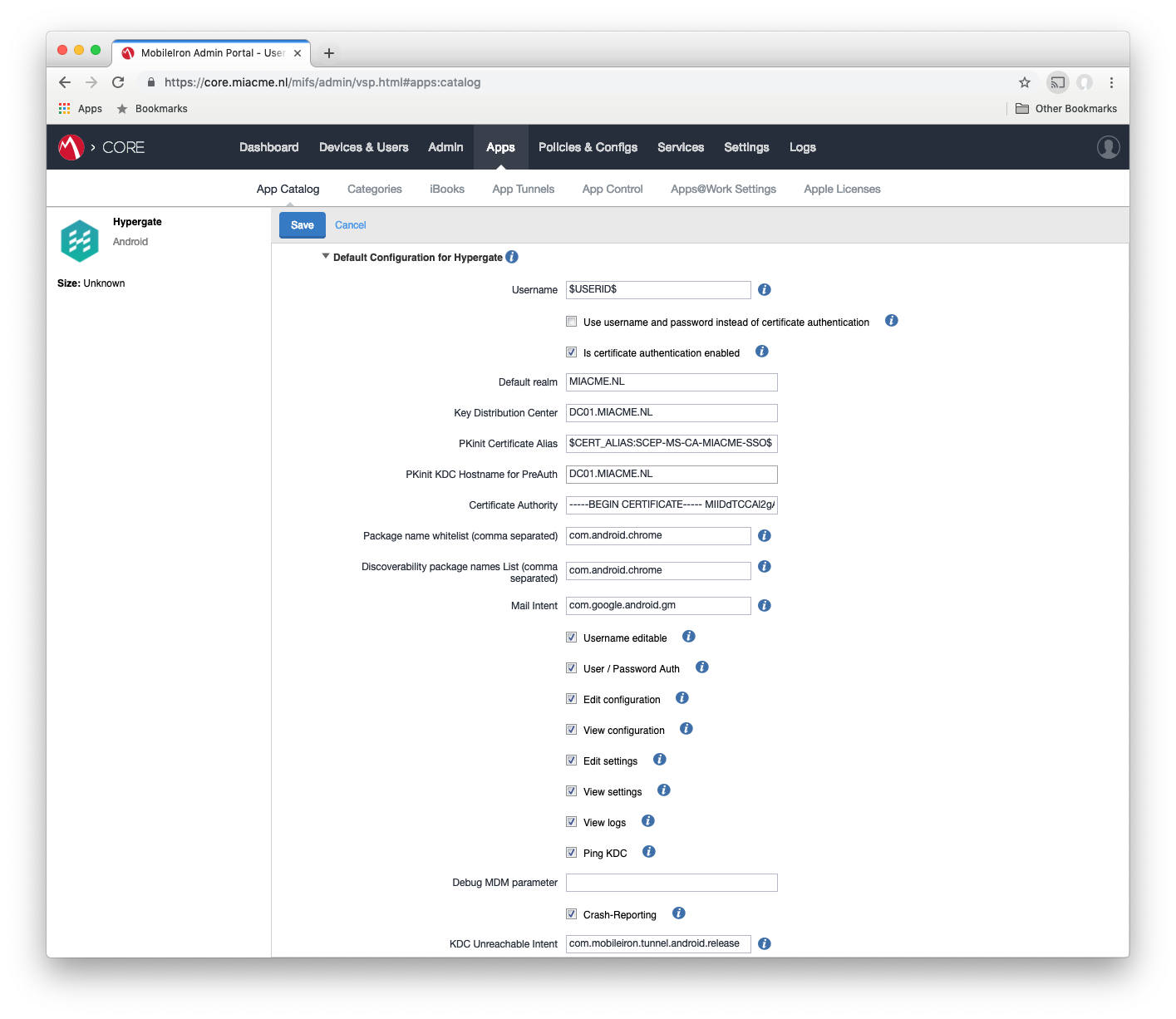
The tick boxes control the menu displayed in the app, for production usage they should be all unticked (user only sees the ticket status), for troubleshooting/setup they can all be ticked (all menus/logging is shown).
When finished, click Save/Finish.
Configure MobileIron Tunnel
#As a reminder, MobileIron Tunnel should be configured correctly and able to reach internal hosts (Chrome needs to reach intranet sites and Hypergate needs to communicate with the KDC). If using the configurations AllowedAppList and DisallowedAppList please ensure they’re configured correctly to allow Chrome and Hypergate to reach their targets.
These apps need assigning
#If not already assigned to a label, please do so now for Tunnel, Chrome and Hypergate. A test label is highly recommended prior to production rollout!
Test Hypergate
#Hypergate is now ready to be tested.
Assigned devices should now have Chrome, Tunnel and Hypergate installed and configured. To validate if Hypergate works correctly, simply open the app and tap “Login”, this should directly show the UPN/Username of the assigned user and current status.
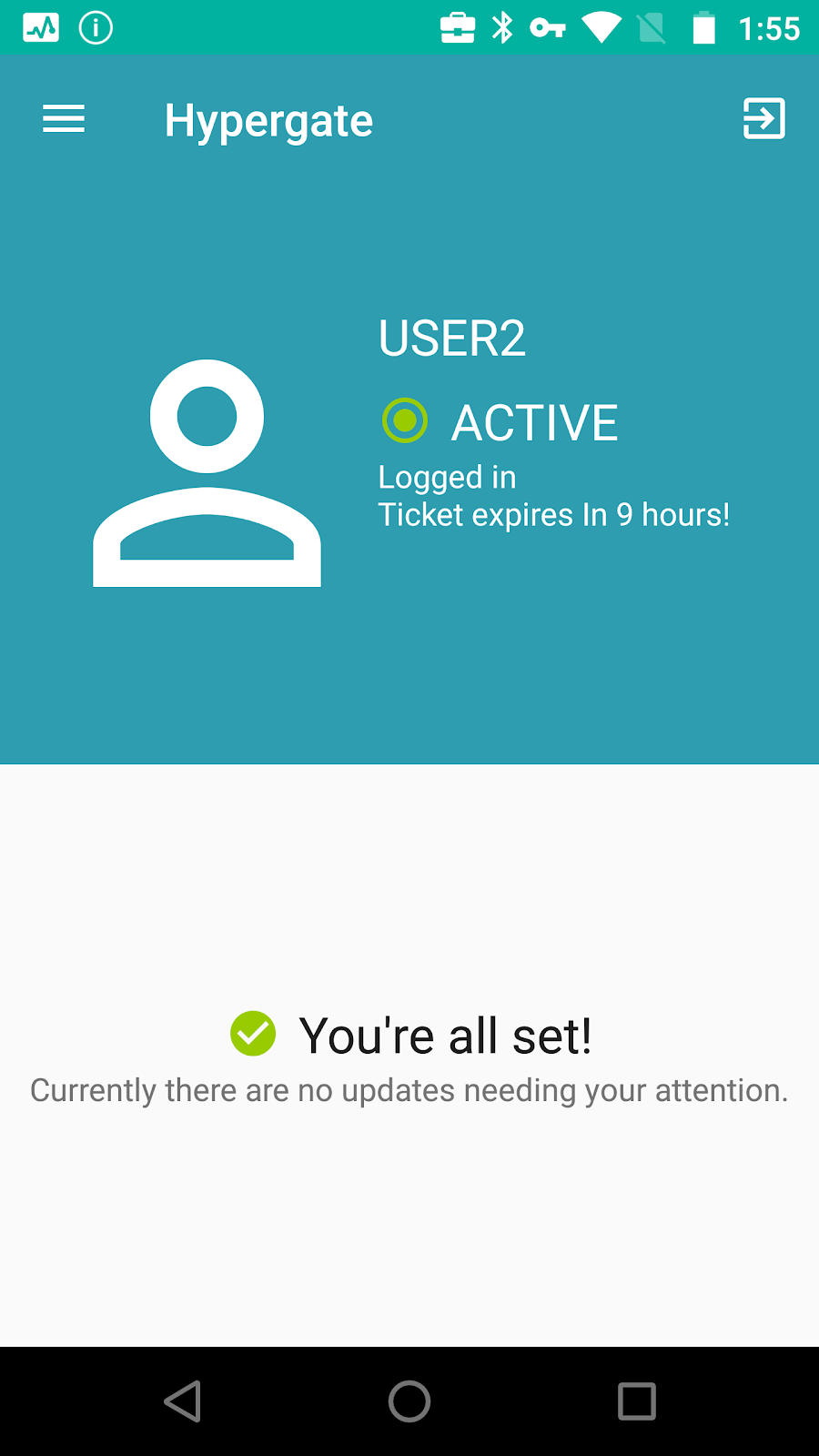
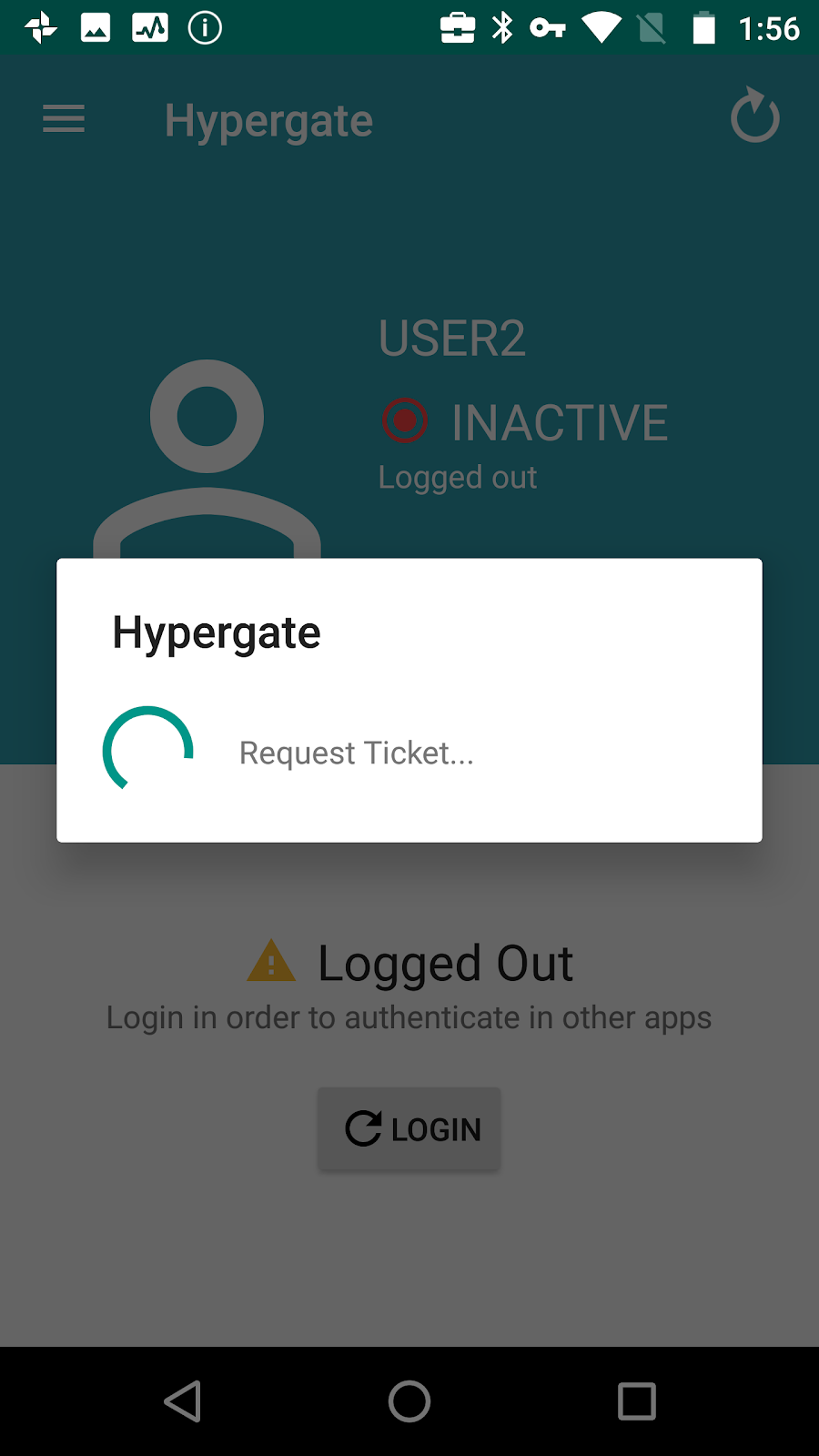
If the login does not work immediately, please check the logging section of Hypergate so troubleshoot (there are also network troubleshooting tools integrated in the “Ping KDC” menu).
Chrome will do this automatically
#Hypergate is only being opened manually to test the functionality. In future, Chrome will launch Hypergate and attempt to authenticate automatically
Test Chrome
#Within Chrome simply navigate to a website that requires authentication. Login should initiate automatically, immediately.
The first time Hypergate needs to fetch a Ticket Granting Ticket (TGT) there will be a non-intrusive short Hypergate prompt, every subsequent request will pass through without showing anything to the user.
Complete!
#At this point Hypergate should be set up correctly and Kerberos authentication will in future work correctly with Android Enterprise.
With this setup it’s equally possible to enable Kerberos SSO for all apps that use Custom Chrome Tabs for authentication (e.g. Slack, Evernote,…).
Other Apps like Microsoft Edge Browser or Brave Browser will require configuration similar to that of Chrome.
Support
#For any additional information about Hypergate or its capabilities, please contact hi@hypergate.com directly.
Docs
General
- Introduction
- What is Android Enterprise?
- Android versions matrix
- Considerations when migrating from device administrator to Android Enterprise
- Android Enterprise feature requests
- What is Android Enterprise Recommended?
- Android Enterprise FAQ
- Android Enterprise device testing
- What is Private Space in Android 15, and how can organisations manage it?
- Why don't all Android devices come with GMS?
- What is Android One?
- Android Enterprise vs Device Admin: Why DA is no longer suitable
- Considerations for choosing Android in the Enterprise
- Feature spotlight: Android Smartlock
- Android glossary
- Android version evolution graphics
- Infobyte: Device Admin deprecation
- How to submit a device for Android Enterprise Recommended validation
- How to view software version information
- How to capture a bug report and device logs
- Gartner comparison of security controls for mobile devices 2019
Provisioning
- How to become a zero-touch enrolment reseller
- What is Android zero-touch enrolment?
- Android Enterprise zero-touch console administration guide
- Android Enterprise DPC identifier collection
- Android Enterprise provisioning guides
- Android Enterprise zero-touch DPC extras collection
- Infobyte: Android Enterprise deployment scenarios
- Infobyte: Android Enterprise fully managed provisioning methods
- Manual Android Enterprise work-managed QR code generation for MobileIron
Work profile
Fully managed
App management
- Set up Hypergate's Kerberos Authentication on MobileIron Core for Android Enterprise
- Managed Google Play, allowlist or blocklist?
- Considerations when deploying MTD with Android Enterprise
- Why you shouldn't install apps from unknown sources
- Create and manage private apps for Android Enterprise
- What is OEMConfig?
- Create and manage web apps for Android Enterprise
- How to locate a private Android app assigned to an organisation ID
- How to host enterprise apps outside of Google Play
- The Google Play iFrame app approval flow is deprecated
- Android 13 adds notifications access as a runtime permission
- Android 14 blocks apps targeting old Android versions
- Android 13 & up restricts permissions when apps are sideloaded
- Android system apps database
- How to resolve common Android app install failures, by error message
FAQ
- Is Android Enterprise supported on uncertified (non-GMS) devices?
- Can apps be sideloaded into the Private Space?
- Is Private Space supported on fully managed devices?
- Why don't Private Space apps go through VPN?
- Is it possible to manage personal applications on a work profile device?
- Does Samsung support Android Enterprise?
- How can apps be managed in the Private Space?
- Are Private Space apps visible to enterprise admins?
- Are Private Space applications truly hidden?
- Why has USB data access been disabled suddenly?
- What versions of Android support Android Enterprise?
- Is it possible to manage eSIM?
- How to check if an Android device is GMS/Play Protect certified?
- To use Android Enterprise do I need to buy Google Workspace (G Suite) and register my domain?
- What devices should I buy for my organisation?
- If Android Enterprise is supported from Lollipop, why is Marshmallow often mentioned instead?
- What’s the difference between Device Admin and Android Enterprise?
- What is the Android Enterprise bind?
- Can I change the account I used to bind Android Enterprise?
- Is it possible to bind Android Enterprise with multiple EMMs using one account?
- How do I remove the Android Enterprise bind from my current EMM?
- What is Android Enterprise Recommended?
- My AER device doesn’t work properly with Android Enterprise, what should I do?
- Is Android One better than AER? (Or the other way around?)
- How do I configure Google Workspace domains for provisioning?
- What’s the best provisioning method?
- What’s the difference between allow adding accounts vs allow configure credentials?
- Is it possible to utilise multiple VPN connections within a profile?
- Is it possible to utilise a single VPN connection across the entire device?
- Does Android support Kerberos natively?
- What’s the difference between device based accounts and user based accounts?
- How do I manage the new notifications runtime permission in Android 13?
- Can organisations see applications outside of the work profile?
- Can organisations deploy applications to the parent profile in a work profile deployment?
- Is it possible to migrate from DA to AE work profile without a re-enrol?
- What is a work challenge?
- Enrolment failed but the work profile was created. How do I remove it?
- Why can’t I install or uninstall apps on my managed device?
- How can I provision a fully managed device?
- Is it possible to “retire” (or enterprise wipe) a fully managed device?
- Devices factory reset as soon as they’re enrolled, why?
- Is Factory Reset Protection enabled on fully managed devices?
- Is it possible to migrate fully managed devices between EMM solutions?
- How has COPE changed in Android 11?
- Does Intune support COPE?
- Can organisations see applications outside of the work profile on a COPE device?
- Can organisations deploy applications to the parent profile in a COPE deployment?
- Is it possible to migrate from fully managed to work profiles on fully managed devices?
- How should system applications be handled on a COPE device?
- What OEMs currently support zero-touch?
- Where are zero-touch resellers located?
- Does zero-touch cost anything?
- Is an EMM still required with zero-touch?
- What happens if a fully set up device is added to the zero-touch console?
- What happens if a user starts setting up a device before the zero-touch config is applied?
- What happens if a zero-touch config is removed from an enrolled device?
- What happens if a new config for a different EMM or server is applied to an enrolled device?
- Can I add/remove users on a fully managed device?
- How can I access a Wi-Fi captive portal when devices are in Kiosk?
- My AMAPI project returns a usage limit error, why?
- What happens if a zero-touch assigned device is reset?
- What happens if a device is unregistered from the zero-touch console?
- Can a device be OTA managed from the zero-touch console?
- Does enrolling via zero-touch slow down or cause any delay to the setup process while it’s retrieving the zero-touch config?
- What deployment scenario will a zero-touch device enrol under?
- Why does zero-touch require so much touching?
- Can anyone add a device to the zero-touch console?
- Is it possible for an organisation to add previously-purchased devices to zero-touch?
- Can a MADA device be converted to EDLA?
- Can anyone remove a device from the zero-touch console?
- Does Samsung support zero-touch?
- Is it possible to set a zero-touch default configuration?
- Is it possible to bulk update zero-touch devices?
- Is it possible to change zero-touch resellers?
- Are all zero-touch devices Android Enterprise Recommended?
- What are DPC extras?
- What should I put in DPC extras?
- What happens if a device is uploaded to zero-touch with the wrong manufacturer?
- The device registered with zero-touch, but doesn’t launch during setup, why?
- Does Android Go support zero-touch?
- Are employee-owned devices eligible for zero-touch?
- What’s the recommended way of managing private (in-house) applications?
- How do I turn off Google Play app collections?
- Is it possible to deploy app shortcuts to the homescreen of an Android Enterprise device?
- Is it possible to backup & restore device data on a fully managed device?
- The Google Play iFrame is missing a feature in my UEM. How do I enable it?
- How do I configure allowlist/blocklist domains for Google Chrome?
- How to configure Chrome managed bookmarks
- Play Protect blocked my DPC, why?